Establish connections with remote computers using the secure shell, (SSH)
One of Linux's most interesting features is the ability to competently use a computer with nothing, but commands entered into the keyboard and better yet, to be able to do that on computers that are located anywhere in the world, be it a physical server or a virtual machine. The physical servers may be located in a company’s private data center, or a public cloud like Amazon Web Services (AWS), Microsoft Azure, Google Compute Platform (GCP), or any other cloud provider. It does not matter where the computer is located. What matters is that you can connect to those servers and work on them.
Thanks to OpenSSH, users can open a secure shell on any computer they have permission to access and use from a remote location. It's a daily job for many Linux users, but it can be puzzling for someone who has yet to try it. In this piece, I will explain how to configure two computers for secure shell (SSH) connections, and how to securely connect from one server to the other without password authentication.
Technical Jargon
When discussing more than one computer, it can be puzzling to identify one from the other. The Tech world has well-established standards to help clarify explanations of the process of networking computers together.
- Service: A service is software that runs in the background so it can be used by computers other than the one it's installed on. For example, a web server hosts a web-sharing service.
- Host: A host is any computer. In IT, computers are called hosts because technically any computer can host an application that's useful to some other computers. You may not think of your laptop as a "host," but you're likely running some service that's useful to you, your mobile, or some other computers.
- Local: The local computer is the one you or some software program is using. Every computer refers to itself as localhost, for instance.
- Remote: A remote computer is one you're not physically in front of or physically using. It's a computer in a remote location.
Now that
the technical jargon has been taken care of, let’s begin.
Activate SSH on each host
For two computers to be connected over SSH, each host must have SSH installed. SSH has two components: the command you use on your local machine to start a connection, (SSH Client is installed on this server) and a
server to accept incoming connection requests (SSH Server is installed on this server). Some computers come with one or both parts of SSH already installed.
For this article, I am going to use two servers with the following hostnames:
- uta.com (Local Server, this will act as SSH Client)
- uta.com (Remote Server, this will act as SSH Server)
The commands vary, depending on your system, to confirm whether you have both the command and the server installed, the easiest way is to look for the relevant configuration files:
On both servers, run the following command to check what type of file the file is:
$ file /etc/ssh/ssh_config
Should this return a
No such file or directory error, then you don't have the SSH command installed:
On server 1 utadev01.uta.com, the command returned an error:
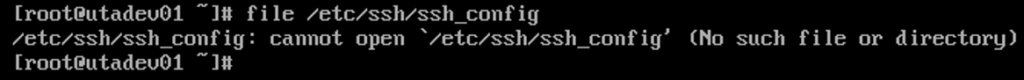
On server 2 utadev02.uta.com, the command returned an error, see Fig. 2 below:
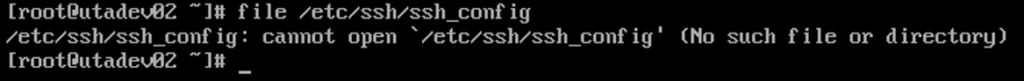
Also, if you try to SSH to the server using an SSH client like Putty, you will receive a network connection error.
Do alike, check for the SSH service (note the
d in the filename):
$ file /etc/ssh/sshd_config
On server 1 utadev01.uta.com, the command returned an error as seen in Fig. 4 below:
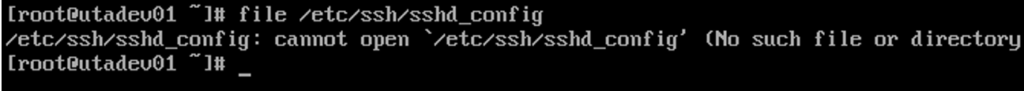
On server 1 utadev02.uta.com, the command returned an error as seen in Fig. 5 below:
 Which host is the server, and which one is the client?
Which host is the server, and which one is the client?
SSH is role-based, so no one can say this is the client and that is the server. Both can be client and server depending on the role each is
playing at any particular point in time. At one point,
utadev01.uta.com may be the
localhost where the SSH Client package is installed,
while
utadev02.uta.com may be the remote server where the SSH Server package is installed and vice-versa.
Generally speaking, both the SSH client package and the SSH server package are installed in all Linux servers, so that any of the servers will
be able to perform client-server role depending on situations.
Install one or the other, as needed.
In this lab, I am going to install, both packages in all servers, using the command below.
$ sudo dnf install openssh-clients openssh-server -y
On both servers, enable the SSH service with systemd:
$ sudo systemctl enable --now sshd
Now that you've installed and enabled SSH on both servers, you can try logging in with a password as a test. To access the remote computer,
you must have a username and a password.
Your remote user doesn't have to be the same as your local user. You can log in as any user on the remote machine if you have that user's password.
For example, I'm
student on my work local host, but I'm
richard on the remote server. If I'm on my localhost and I want to SSH into the remote server,
I can do that by identifying myself as
richard and using my password at the remote server.
To SSH into the remote computer, you must know its internet protocol (IP) address or its resolvable hostname. To find the remote server's IP address,
use the ip command (on the remote server):
$ ip addr show | grep "inet"
See Fig. 6 below:
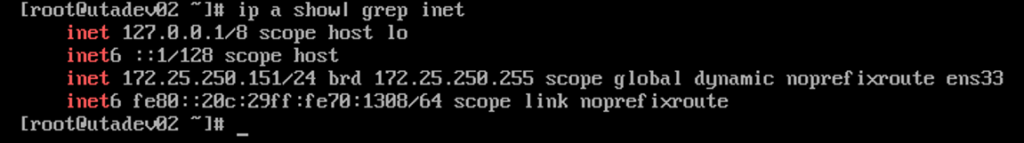
From the above screenshot, you can see that the IP address is 172.25.250.151
If the remote computer doesn't have the
IP command, try
ifconfig instead.
The address 127.0.0.1 is a special one and is, in fact, the address of
localhost. It's a "loopback" address, which your system uses to reach itself.
That's not useful when logging into a remote machine, so in this example, the remote computer's correct IP address is 172.25.250.151. In real life,
I would know that because my local network uses the 172.25.250.0 subnet. If the remote server is on a different network, then the
IP address could be nearly anything (but will never be 127.0.0.1), and some special routing is probably necessary to reach it through various firewalls.
If you can ping the remote machine by its IP address
or its resolvable hostname, and have a login account on it, then you can SSH into it:
$ ping -c3 172.25.250.151
$ ping -c3 utadev02.uta.com
 That's a success. Now use SSH to log in:
That's a success. Now use SSH to log in:
$ whoami
student
$ ssh
richard@172.25.250.151
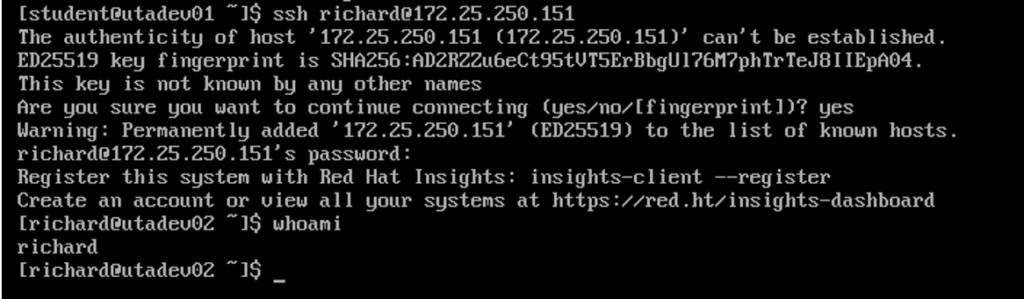
bash$ whoami
richard
The test login works, so now you're ready to activate passwordless login.
Create an SSH key
To log in securely to another computer without a password, you must have an SSH key. You may already have an SSH key,
but it doesn't hurt to create a new one. An SSH key begins its life on your local machine. It consists of two components: a private key, which you never share with anyone or anything, and a public one, which you copy onto any remote machine you want to have passwordless access to.
Some people create one SSH key and use it for everything from remote logins to GitHub authentication. In this example, I'll create a unique key to use on computers within my local area network.
To create a new SSH key, use the ssh-keygen command:
$ ssh-keygen
You will be shown the file location of your private key and what the name of the private key should be. Since we did not specify the type of key to be created, the default rsa key type will be created with a default name id_rsa. Press enter to accept the key name and location. You'll be prompted to create passphrase, aka as a password for your SSH key. Just press enter twice to skip providing passphrase. Although, in an ideal situation, you should create a password for the key. This means you'll have to enter a password when using the key, but that password remains local and isn't transmitted across the network. After running this command, you're left with an SSH private key called
id_rsa and an SSH public key called
id_rsa.pub
Your screen should look like the screenshot below:
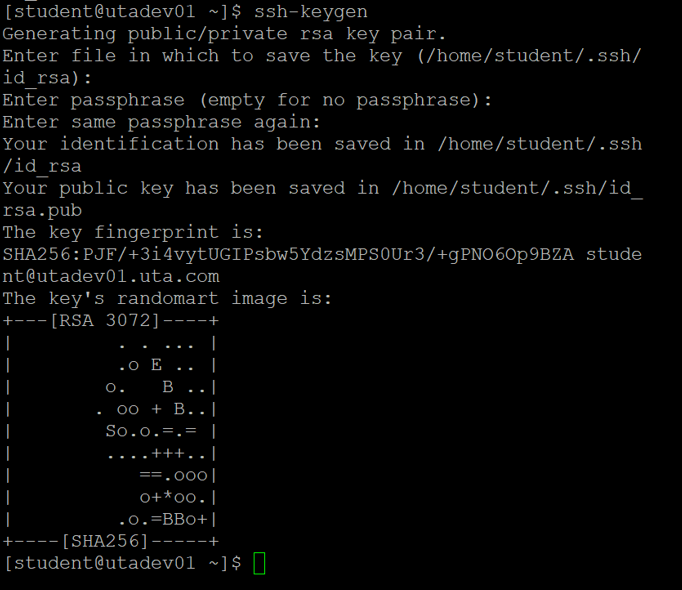
To get the public key over to your remote machine, use the
ssh-copy-id. For this to work, you must verify that you have SSH access to the remote machine.
If you can't log into the remote host with a password, you can't set up passwordless login either:
$ ssh-copy-id richard@172.25.250.151
During this process, you'll be prompted for your login password for the user
richard on the remote host.
Your screen should look like the screenshot below:
 Upon success, try logging in again as follows:
Upon success, try logging in again as follows:
$ ssh richard@172.25.250.151
bash$ whoami
richard
Your screen should look like this:
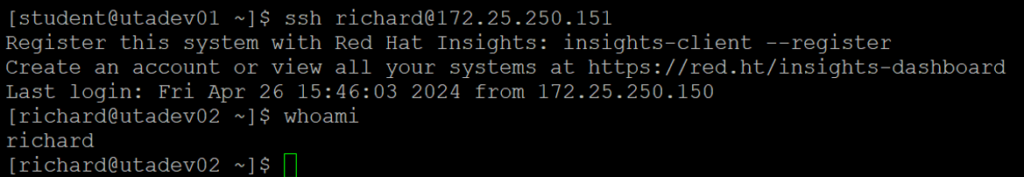
Once you have passwordless authentication set up, you can edit the
/etc/ssh/sshd_config file to disallow password authentication.
This prevents anyone from using SSH to authenticate to a computer unless they have your private key. To do this, open
/etc/ssh/sshd_config
file in a text editor with
sudo permissions and search for the string
PasswordAuthentication. Change the default line to look as below.
PasswordAuthentication no
Save it and restart the SSH server (or just reboot):
$ sudo systemctl restart sshd && echo "OK"
OK
Using SSH every day
OpenSSH changes your view of computing. No longer are you bound to just the computer in front of you. With SSH, you have access to
any computer in your house, or servers you have accounts on, and even mobile and Internet of Things devices. Unlocking the power of SSH
also unlocks the power of the Linux terminal. If you're not using SSH every day, start now. Get comfortable with it, collect some keys,
live more securely, and expand your world.
***** WE LEARN IT BY DOING ***** On server 2 utadev02.uta.com, the command returned an error, see Fig. 2 below:
On server 2 utadev02.uta.com, the command returned an error, see Fig. 2 below:
 Also, if you try to SSH to the server using an SSH client like Putty, you will receive a network connection error.
Do alike, check for the SSH service (note the d in the filename):
$ file /etc/ssh/sshd_config
On server 1 utadev01.uta.com, the command returned an error as seen in Fig. 4 below:
Also, if you try to SSH to the server using an SSH client like Putty, you will receive a network connection error.
Do alike, check for the SSH service (note the d in the filename):
$ file /etc/ssh/sshd_config
On server 1 utadev01.uta.com, the command returned an error as seen in Fig. 4 below:
 On server 1 utadev02.uta.com, the command returned an error as seen in Fig. 5 below:
On server 1 utadev02.uta.com, the command returned an error as seen in Fig. 5 below:
 From the above screenshot, you can see that the IP address is 172.25.250.151
If the remote computer doesn't have the IP command, try ifconfig instead.
The address 127.0.0.1 is a special one and is, in fact, the address of localhost. It's a "loopback" address, which your system uses to reach itself.
That's not useful when logging into a remote machine, so in this example, the remote computer's correct IP address is 172.25.250.151. In real life,
I would know that because my local network uses the 172.25.250.0 subnet. If the remote server is on a different network, then the
IP address could be nearly anything (but will never be 127.0.0.1), and some special routing is probably necessary to reach it through various firewalls.
If you can ping the remote machine by its IP address or its resolvable hostname, and have a login account on it, then you can SSH into it:
$ ping -c3 172.25.250.151
$ ping -c3 utadev02.uta.com
From the above screenshot, you can see that the IP address is 172.25.250.151
If the remote computer doesn't have the IP command, try ifconfig instead.
The address 127.0.0.1 is a special one and is, in fact, the address of localhost. It's a "loopback" address, which your system uses to reach itself.
That's not useful when logging into a remote machine, so in this example, the remote computer's correct IP address is 172.25.250.151. In real life,
I would know that because my local network uses the 172.25.250.0 subnet. If the remote server is on a different network, then the
IP address could be nearly anything (but will never be 127.0.0.1), and some special routing is probably necessary to reach it through various firewalls.
If you can ping the remote machine by its IP address or its resolvable hostname, and have a login account on it, then you can SSH into it:
$ ping -c3 172.25.250.151
$ ping -c3 utadev02.uta.com
 That's a success. Now use SSH to log in:
$ whoami
student
$ ssh richard@172.25.250.151
That's a success. Now use SSH to log in:
$ whoami
student
$ ssh richard@172.25.250.151
 bash$ whoami
richard
The test login works, so now you're ready to activate passwordless login.
Create an SSH key
To log in securely to another computer without a password, you must have an SSH key. You may already have an SSH key,
but it doesn't hurt to create a new one. An SSH key begins its life on your local machine. It consists of two components: a private key, which you never share with anyone or anything, and a public one, which you copy onto any remote machine you want to have passwordless access to.
Some people create one SSH key and use it for everything from remote logins to GitHub authentication. In this example, I'll create a unique key to use on computers within my local area network.
To create a new SSH key, use the ssh-keygen command:
$ ssh-keygen
You will be shown the file location of your private key and what the name of the private key should be. Since we did not specify the type of key to be created, the default rsa key type will be created with a default name id_rsa. Press enter to accept the key name and location. You'll be prompted to create passphrase, aka as a password for your SSH key. Just press enter twice to skip providing passphrase. Although, in an ideal situation, you should create a password for the key. This means you'll have to enter a password when using the key, but that password remains local and isn't transmitted across the network. After running this command, you're left with an SSH private key called id_rsa and an SSH public key called id_rsa.pub
Your screen should look like the screenshot below:
bash$ whoami
richard
The test login works, so now you're ready to activate passwordless login.
Create an SSH key
To log in securely to another computer without a password, you must have an SSH key. You may already have an SSH key,
but it doesn't hurt to create a new one. An SSH key begins its life on your local machine. It consists of two components: a private key, which you never share with anyone or anything, and a public one, which you copy onto any remote machine you want to have passwordless access to.
Some people create one SSH key and use it for everything from remote logins to GitHub authentication. In this example, I'll create a unique key to use on computers within my local area network.
To create a new SSH key, use the ssh-keygen command:
$ ssh-keygen
You will be shown the file location of your private key and what the name of the private key should be. Since we did not specify the type of key to be created, the default rsa key type will be created with a default name id_rsa. Press enter to accept the key name and location. You'll be prompted to create passphrase, aka as a password for your SSH key. Just press enter twice to skip providing passphrase. Although, in an ideal situation, you should create a password for the key. This means you'll have to enter a password when using the key, but that password remains local and isn't transmitted across the network. After running this command, you're left with an SSH private key called id_rsa and an SSH public key called id_rsa.pub
Your screen should look like the screenshot below:
 To get the public key over to your remote machine, use the ssh-copy-id. For this to work, you must verify that you have SSH access to the remote machine.
If you can't log into the remote host with a password, you can't set up passwordless login either:
$ ssh-copy-id richard@172.25.250.151
During this process, you'll be prompted for your login password for the user richard on the remote host.
Your screen should look like the screenshot below:
To get the public key over to your remote machine, use the ssh-copy-id. For this to work, you must verify that you have SSH access to the remote machine.
If you can't log into the remote host with a password, you can't set up passwordless login either:
$ ssh-copy-id richard@172.25.250.151
During this process, you'll be prompted for your login password for the user richard on the remote host.
Your screen should look like the screenshot below:
 Upon success, try logging in again as follows:
$ ssh richard@172.25.250.151
bash$ whoami
richard
Your screen should look like this:
Upon success, try logging in again as follows:
$ ssh richard@172.25.250.151
bash$ whoami
richard
Your screen should look like this:
 Once you have passwordless authentication set up, you can edit the /etc/ssh/sshd_config file to disallow password authentication.
This prevents anyone from using SSH to authenticate to a computer unless they have your private key. To do this, open /etc/ssh/sshd_config
file in a text editor with sudo permissions and search for the string PasswordAuthentication. Change the default line to look as below.
PasswordAuthentication no
Save it and restart the SSH server (or just reboot):
$ sudo systemctl restart sshd && echo "OK"
OK
Using SSH every day
OpenSSH changes your view of computing. No longer are you bound to just the computer in front of you. With SSH, you have access to
any computer in your house, or servers you have accounts on, and even mobile and Internet of Things devices. Unlocking the power of SSH
also unlocks the power of the Linux terminal. If you're not using SSH every day, start now. Get comfortable with it, collect some keys,
live more securely, and expand your world.
***** WE LEARN IT BY DOING *****
Once you have passwordless authentication set up, you can edit the /etc/ssh/sshd_config file to disallow password authentication.
This prevents anyone from using SSH to authenticate to a computer unless they have your private key. To do this, open /etc/ssh/sshd_config
file in a text editor with sudo permissions and search for the string PasswordAuthentication. Change the default line to look as below.
PasswordAuthentication no
Save it and restart the SSH server (or just reboot):
$ sudo systemctl restart sshd && echo "OK"
OK
Using SSH every day
OpenSSH changes your view of computing. No longer are you bound to just the computer in front of you. With SSH, you have access to
any computer in your house, or servers you have accounts on, and even mobile and Internet of Things devices. Unlocking the power of SSH
also unlocks the power of the Linux terminal. If you're not using SSH every day, start now. Get comfortable with it, collect some keys,
live more securely, and expand your world.
***** WE LEARN IT BY DOING *****
